Let's Encrypt adalah otoritas sertifikat yang menyediakan sertifikat SSL gratis untuk situs web untuk mengaktifkan enkripsi TLS. Diluncurkan pada April 2016.
Let's Encrypt mengotomatiskan proses pembuatan sertifikat, validasi, penandatanganan, penerapan, dan pembaruan sertifikat untuk situs web yang aman.
Saat ini, Let's encrypt mendukung penerbitan sertifikasi otomatis untuk Apache, Nginx, Plex, dan Haproxy.
Prasyarat
Anda harus memiliki tumpukan LEMP yang dikonfigurasi pada sistem RHEL / CentOS Anda.
BACA :Cara Memasang LEMP Stack di CentOS 8 / RHEL 8
BACA: Cara Memasang LEMP Stack di CentOS 7 / RHEL 7
Instal Certbot
Untuk menghasilkan sertifikat Let's Encrypt untuk domain Anda, Anda harus memiliki akses terminal, dan klien Certbot ACME diinstal pada sistem Anda. Ini menangani penerbitan sertifikat dan memperbarui konfigurasi Nginx untuk menggunakan sertifikat yang dibuat tanpa waktu henti.
Certbot tersedia di repositori EPEL hanya untuk CentOS 7 / RHEL 7. Jadi, kita perlu mengunduh installer Certbot secara manual untuk CentOS 8 / RHEL 8 dari situs resminya.
### CentOS 8 / RHEL 8 ### curl -O https://dl.eff.org/certbot-auto mv certbot-auto /usr/local/bin/certbot-auto chmod 0755 /usr/local/bin/certbot-auto ### CentOS 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm yum install -y certbot python2-certbot-nginx ### RHEL 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm subscription-manager repos --enable rhel-7-server-optional-rpms yum install -y certbot python2-certbot-nginx
Buat Virtualhost
Sekarang kita akan membuat file konfigurasi virtual host (server block) untuk domain www.itzgeek.net.
Blok server ini melayani versi HTTP domain Anda.vi /etc/nginx/conf.d/www.itzgeek.net.conf
Gunakan informasi di bawah ini.
server {
server_name www.itzgeek.net;
root /opt/nginx/www.itzgeek.net;
location / {
index index.html index.htm index.php;
}
access_log /var/log/nginx/www.itzgeek.net.access.log;
error_log /var/log/nginx/www.itzgeek.net.error.log;
location ~ \.php$ {
include /etc/nginx/fastcgi_params;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
} Buat root dokumen untuk menempatkan file HTML Anda.
mkdir -p /opt/nginx/www.itzgeek.net
Ubah izin direktori.
chown -R nginx:nginx /opt/nginx/www.itzgeek.net
Tempatkan file HTML uji di root dokumen domain web Anda.
echo "This is a test site @ www.itzgeek.net" > /opt/nginx/www.itzgeek.net/index.html
Mulai ulang layanan Nginx.
systemctl restart nginx
Buat / Perbarui Data DNS
Akses alat manajemen DNS atau Pendaftar domain Anda dan buat data A/CNAME untuk domain tersebut. Contoh:www.itzgeek.net.
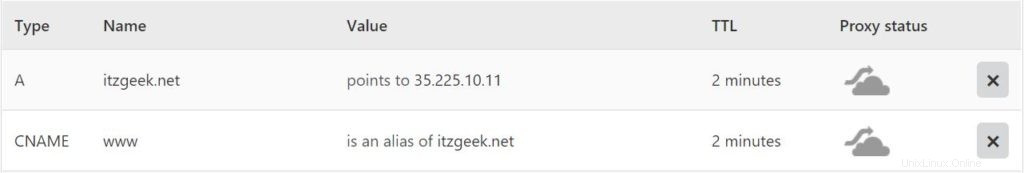
Tunggu beberapa saat hingga rekaman menyebar.
Periksa propagasi DNS dengan utilitas Nslookup yum install -y bind-utils.

Instal Let's Encrypt Certificate
Gunakan perintah certbot untuk membuat dan menginstal sertifikat Let's Encrypt.
### CentOS 8 / RHEL 8 ### /usr/local/bin/certbot-auto --nginx ### CentOS 7 / RHEL 7 ### certbot --nginx
Ikuti perintah interaktif dan buat serta instal sertifikat.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] << Email Address to receive renewal/security notification - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A << Access Terms and Conditions - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y << Subscribe to Newsletter Which names would you like to activate HTTPS for? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: www.itzgeek.net - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate numbers separated by commas and/or spaces, or leave input blank to select all options shown (Enter 'c' to cancel): 1 << Choose domain name to generate certificate Obtaining a new certificate Performing the following challenges: http-01 challenge for www.itzgeek.net Waiting for verification... Cleaning up challenges Deploying Certificate to VirtualHost /etc/nginx/conf.d/www.itzgeek.net.conf Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 << Redirect traffic from HTTP to HTTPS Redirecting all traffic on port 80 to ssl in /etc/nginx/conf.d/www.itzgeek.net.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://www.itzgeek.net You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=www.itzgeek.net - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/www.itzgeek.net/privkey.pem Your cert will expire on 2019-11-02. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Arahkan permintaan HTTP non-www ke www HTTPS dengan Nginx (opsional)
Kami sekarang akan mengonfigurasi server Nginx untuk mengarahkan lalu lintas yang datang untuk situs HTTP non-www ke situs WW HTTPS, yaitu http://itzgeek.net>> https://www.itzgeek.net .
Di sini, kita akan menggunakan file konfigurasi yang sama yang kita buat untuk versi HTTP situs untuk melakukan pengalihan situs HTTP non-www ke WW HTTPS.
vi /etc/nginx/conf.d/www.itzgeek.net.conf
Tambahkan informasi di bawah ini di akhir file.
# Redirect NON-WWW HTTP to WWW HTTPS
server {
if ($host = itzgeek.net) {
return 301 https://www.itzgeek.net$request_uri;
}
server_name itzgeek.net;
listen 80;
return 404;
}
Mulai ulang layanan Nginx.
systemctl restart nginx
Firewall
Konfigurasikan firewall untuk mengizinkan permintaan HTTPS.
firewall-cmd --permanent --add-port=443/tcp firewall-cmd --reload
Verifikasi Let's Encrypt Certificate
Verifikasi detail sertifikat Let's Encrypt dengan membuka versi HTTPS situs web Anda.
http://situs-http-AndaATAU
https://your-https-web-site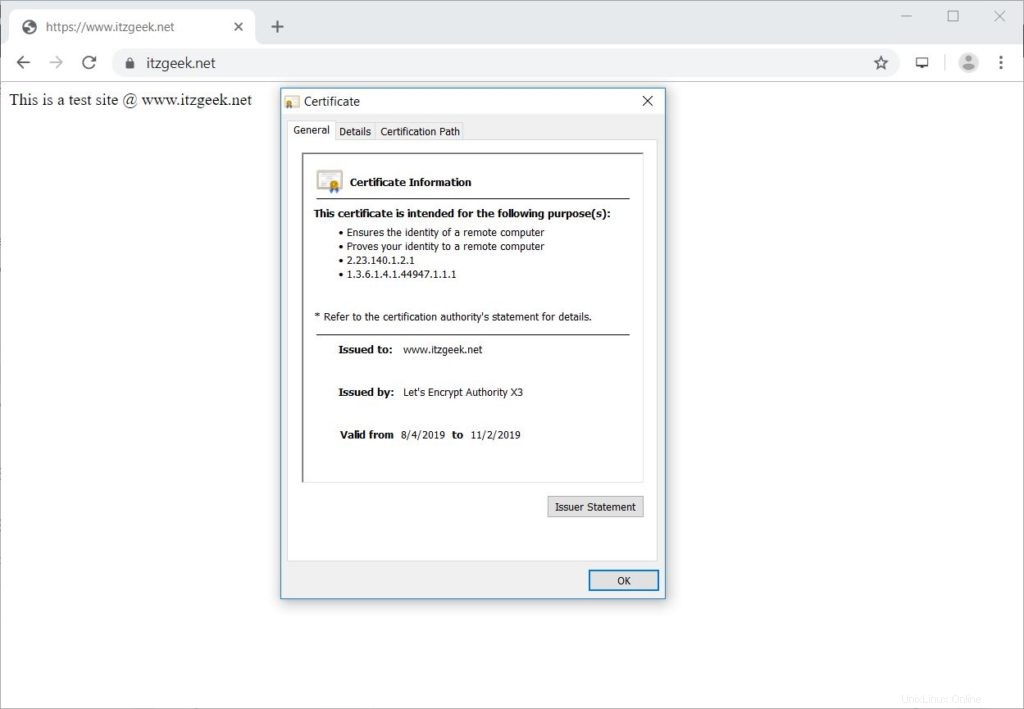
Uji Sertifikat SSL
Periksa sertifikat SSL Anda untuk masalah apa pun dan peringkat keamanannya dengan membuka URL di bawah ini.
https://www.ssllabs.com/ssltest/analyze.html?d=www.itzgeek.net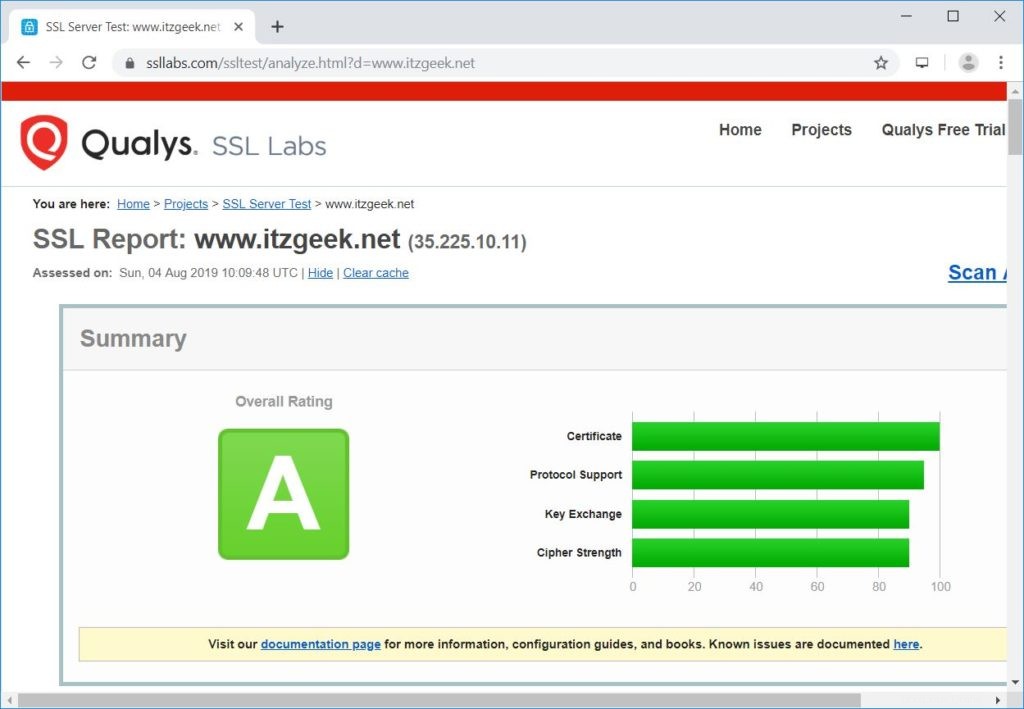
Perbarui Sertifikat Let's Encrypt
Sertifikat Let's Encrypt hadir dengan validitas 90 hari, dan perlu diperbarui sebelum kedaluwarsa.
Secara default, CentOS 7 / RHEL 7 dikonfigurasi dengan entri penjadwal cron yang berjalan dua kali sehari untuk memperbarui sertifikat Let's Encrypt.
Sayangnya, untuk CentOS 8 / RHEL 8, kita perlu mengkonfigurasi cron scheduler secara manual.
echo "0 0,12 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && /usr/local/bin/certbot-auto renew" | sudo tee -a /etc/crontab > /dev/null
Anda juga dapat mensimulasikan proses pembaruan sertifikat dengan perintah di bawah ini untuk memastikan pembaruan berjalan lancar.
### CentOS 8 / RHEL 8 ### /usr/local/bin/certbot-auto renew --dry-run ### CentOS 7 / RHEL 7 ### certbot renew --dry-run
Keluaran:
Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Processing /etc/letsencrypt/renewal/www.itzgeek.net.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Cert not due for renewal, but simulating renewal for dry run Plugins selected: Authenticator nginx, Installer nginx Renewing an existing certificate Performing the following challenges: http-01 challenge for www.itzgeek.net Waiting for verification... Cleaning up challenges - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - new certificate deployed with reload of nginx server; fullchain is /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/www.itzgeek.net/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
Jika keluaran tidak melaporkan masalah apa pun, pembaruan sertifikat akan berfungsi seperti yang diharapkan.
Kesimpulan
Itu saja. Saya harap Anda mempelajari cara menyiapkan Let's Encrypt SSL Certificate with Nginx di CentOS 8 / RHEL 8 &CentOS 7 / RHEL 7. Bagikan tanggapan Anda di bagian komentar.